Using Proxychains-ng
Proxychains is an essential tool used to proxy applications in chained connections
Proxychains-ng comes pre-installed on Kali Linux. If you don'y have it you can install by:
$sudo apt-get install proxychains-ng
This tool is very useful, it can proxy applications in chains to increase anonymity. Also this tool play a vital role in attacking targets, it changes your every 10 or so seconds, this aids in defeating rate limiting. Proxychains can be used with HTTP and SOCKS proxies.
To use proxychains with an CLI application, just type proxychains in front of the command your using
$proxychains nmap -sV -iR 100 -oN [output]
Proxychains has to be properly configured, it also relies TOR
You must install TOR by:
$sudo apt install tor
After installed you can start the service by:
$sudo systemctl enable tor
$service tor start
Now tor is started, now lets add some proxies to the config file, we will use a tool by Corexital Data. This tool takes proxy lists and formats them to be able to be used by proxychains.
Download it here:
Proxychains List Format Script
Python3
Python script to format proxy lists for the proxychains configuration file
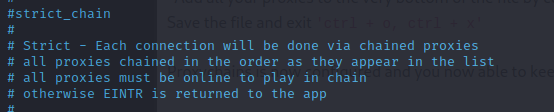
- #Put a hash sign infront of 'strict_chain' if it does not have one
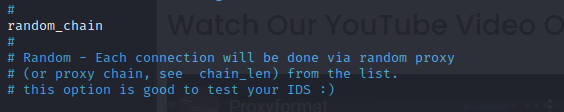
- #Find 'Random_chain' and remove the hash sign
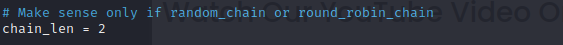
- #Find where it says 'chain_length' and change the value to 4 and remove the hash sign
You can download proxy lists here. Download Proxies
The proxy lists downloaded can't be copy and pasted to the conf file, so we will use 'proxylistformat.py'.
Save the downloaded proxies in the same dir as the python script and run. Follow the prompts and enter neccessary information.
The formatted list will be saved as 'output.txt'. You can copy and paste these proxies to the conf file
To edit the conf file:
$sudo nano /etc/proxychains4.conf
There are alot of options here, as you continue hacking all of this will make much more sense, but for now we will just change to a random, longer chains with all the new downloaded proxies
*Add all your proxies to the very bottom of the file by copying all the proxies in 'output.txt' and pasting them in the file by 'ctrl + shift + v'
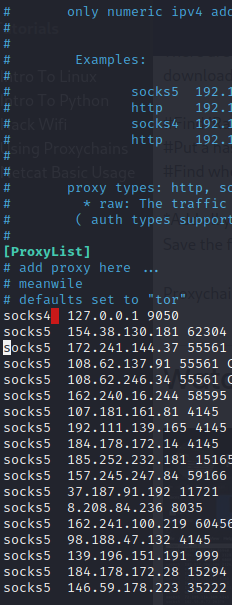
Save the file and exit
'ctrl + o, ctrl + x'
Proxychains is now configured and you now able to keep yourself safe and ready to attack.
