T1561.002 - Disk Wipe: Disk Content Wipe
Tactic: Impact
Platforms: Linux, Network, Windows, macOS
While simple in function, disk wiping (or disk erasure) is deadly. It will be carried out as a malicious tactic by adversaries as the final stage of an attack sequence to deliver significant impact to a victim or organization. Disk content wiping typically relates to the destruction of critical and potentially sensitive data that an organization may have available on its network.

Alongside the destruction of data, wiping may also be carried out to disrupt the operations of an organization or to cover adversaries' tracks. Depending on the goals of the attacker in question, a disk can be partially or completely overwritten using several different tools, some of which we will explore in this tutorial.
There are many ways that hackers may carry out disk wiping for impact:
I) Using Malware
Malware can be delivered through various means such as email attachments, infected websites or compromised software. One notable example of malware designed for disk wiping is Shamoon or ‘Disttrack’ which is often used in targeted attacks against organizations, where the goal is to cause significant damage and disruption to organizations.
II) Remote Access
If a hacker gains unauthorized access to a system, they can remotely execute commands to initiate the disk wiping process. Access may be obtained through the exploiting of vulnerabilities in the system’s security or by using stolen credentials.
III) Scripted Attacks
More technically able hackers may build custom scripts or use additional tools to automate the disk-wiping process across multiple systems simultaneously. Scripts can be tailored to target whole drives or specific directories and files.
IV) Rootkits
Through the use of rootkits, hackers may achieve persistent access and control. Additionally, attackers such as disk wiping will be harder for system admins to detect and mitigate.
V) Bootable Media
USB drives or CDs containing disk wiping tools may be used to bypass the OS’s security measures and directly access the storage devices for wiping.
VI) Insider Threats
Disk wiping attacks may be carried out with the help of incentivized employees or individuals with legitimate access to targeted systems.
VII) Destructive Payloads
In certain cyber-attacks, hackers may include a destructive payload as part of their malware. The code may be designed to initiate disk wiping after carrying out specific objectives, such as exfiltrating sensitive data or causing system disruptions.
In 2011, the paper ‘Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains’ was made available through the Lockheed Martin Corporation by Eric M. Hutchins, Michael J. Cloppert and Rohan M. Amin. The paper provides an in-depth look at a new defence mechanism that can help in understanding adversary campaigns - namely the ‘Cyber-Kill Chain’.
The Cyber Kill Chain is a concept introduced as a framework that describes the stages an attacker typically goes through to successfully compromise a target network or system.
As we are dealing with a tactic that correlates to the final stage of an attack, it will be useful to take a closer look at the full chain so we can understand an attacker’s mindset when completing his objectives with a disk wipe.
There are seven stages of the Cyber Kill Chain:
-
Reconnaissance
‘research, identification and selection of targets’
-
Weaponization
‘coupling an exploit into a deliverable payload, typically through the use of an automated tool or ‘weaponizer’ such as a PDF or Office document’
-
Delivery
‘transmission of the weapon to a targeted environment, often via email attachments, websites and USB sticks’
-
Exploitation
‘the triggering of adversary code, often targeting an application or OS system vulnerability’
-
Installation
‘the installation of a remote access trojan or backdoor on the victim system to maintain persistence in the environment’
-
Command and Control (C2)
‘often, an Internet controller server is used to establish a channel with compromised hosts, once established, intruders have full access inside the target environment’
-
Actions on Objectives
‘once the first six phases have been completed, adversaries can carry out actions to achieve their overall objectives, in this case for the wiping of data from systems’
In the case of disk wiping, ‘availability’ is the affected component of the CIA triad:

One piece of software that can be used as a tool against Windows systems to interact with files, disks and partitions is called 'RawDisk' designed by the EldoS Corporation.
The driver allows for direct modification of data on a local computer’s hard drive. In some instances, the tool can circumvent Windows OS security features.
Defensive measures:
To mitigate against the potentially disastrous occurrence of a disk’s content being wiped, backups are essential.
To help mitigate the risks of disk content wipe attacks, and as part of a more proactive stance against this kind of incident, business continuity plans and disaster recovery plans must be put in place to help restore operations if necessary.
When relevant documents have been prepared and finalised, they should then be stored in a safe, accessible location off-site for their protection.
A range of different backup types can be implemented depending on an organisation’s needs including full, incremental or differential backups or a combination. In all cases, the amount of time that is needed to restore from backups is another aspect to consider as restoring from incremental backups especially can take some time.
The storage location of backups is also an important element to consider, especially if they contain critical or sensitive data. Ideally, encryption keys should also be used for enhanced security.
Alongside mitigation strategies for preserving important data, a variety of detection strategies can and should be implemented on a system.
These include:
- -->Command execution (e.g. cipher.exe)
- -->Drive access and modification
- -->Driver load
- -->Process creation
On Windows, the ‘CHKDSK’ tool (short for ‘check disk’) is a useful utility that can scan a computer hard drive in search of system errors amongst other abilities, in the name of good computer hygiene.
To initialize it from the command line (you need to be admin), you can simply enter ‘chkdsk’ for operation in read-only mode, ‘chkdsk /f’ to fix errors on the disk and ‘chkdsk /r’ to locate bad sectors and recover readable information.
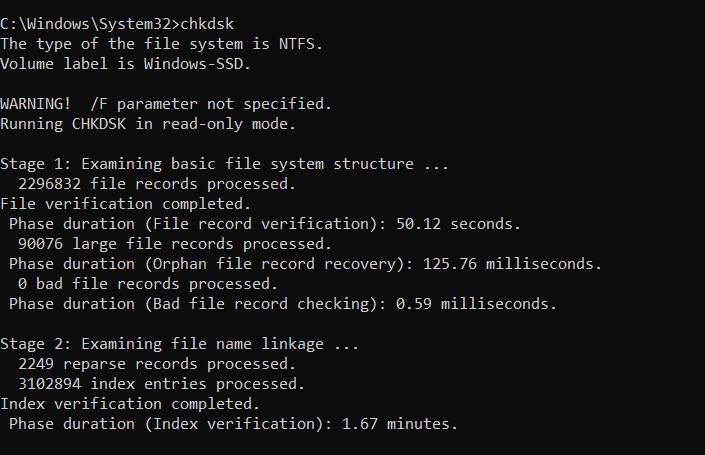
The utility is a system tool that verifies file system integrity whilst fixing logical file system errors.
For more information about the chkdsk utility including possible parameters, see Microsoft’s guide here.
In Linux, the equivalent is the ‘fsck’ command which can also be used to check and repair the filesystem.
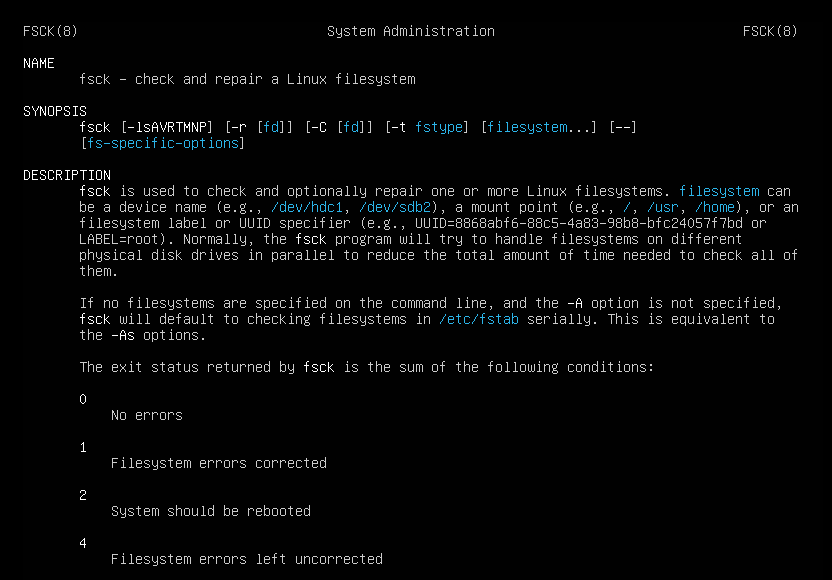
All in all, if a disk-wiping attack occurs within your organisation, it’s safe to say you have a problem - especially if you don’t have good backups ready to be deployed.
Some of the negative consequences of disk-wiping attacks include:
- data loss
- operational downtime
- financial losses
- reputational damage
Case Study:
On the 15th of August, 2012 the Shamoon virus infiltrated the networks of the national oil company ‘Saudi Aramco’. Noted as one of the most destructive cyber attacks initiated against a single business at the time, the hack involved a $50 million ransom demand.
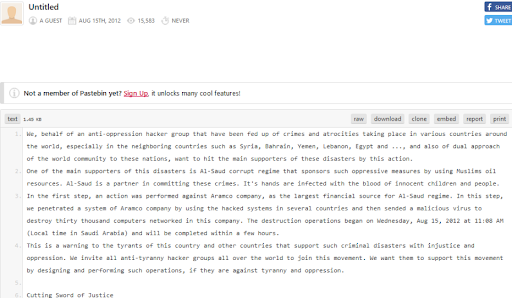
The virus spread through the company, wiping hard drives in the process leading to the destruction of over 30,000 computers. To restore operations, Aramco had to purchase many of the world’s hard drives to get operations back on track.
In this case, the malware (also known as Disttrack) had three components to carry out its objectives:
- Dropper (built in both 32 and 64-bit)
- Wiper
- Reporter
Looking more closely at the wiper element, it was the inclusion of ‘RawDisk’ that enabled the direct modification of data on computer hard drives.
The driver was used to write to protected system locations such as the Master Boot Record and disk partitions to destroy data.
RawDisk has also been used to directly access hard disks to help overwrite arbitrarily sized portions of disk content. (Content wipe).
Since the event in 2012, the malware has been used in several more high-profile attacks.
For further reading on the Shamoon virus see:
https://attack.mitre.org/software/S0140/,
https://www.bbc.co.uk/news/technology-192
