T1040 - Network Sniffing
Tactics: Discovery, Credential Access
Platforms: IaaS, Linux, Windows, macOS
Depending on who is carrying it out, network sniffing (sometimes referred to as ‘packet’ sniffing) can either be a useful source of information or a sizeable security concern. In the MITRE ATT&CK framework, the technique can be used both for credential access and discovery purposes. In the past, sniffing was restricted to be carried out by engineers with access to specialized hardware devices. Today, there are numerous pieces of software which can aid an adversary in carrying it out.
Below is an example of a physical network tap that can be used for sniffing a network:

A Dualcomm ETAP-2003 network tap
In the case of the above-pictured ETAP-2003, to capture real-time data traffic, you would insert it inline between devices on a network. For example, between a switch and a VoIP system and a computer used for monitoring purposes on the other side. This particular device can be powered from a laptop’s USB port, has built-in current limiting and works with PoE (Power over Ethernet) so as not to block any end-to-end flow of inline power.
Network sniffing can be a useful practice for a network engineer, for the following purposes:
- Network troubleshooting
- sniffing to monitor and diagnose network problems - Performance monitoring
- analyzing network performance and identifying bottlenecks - Data gathering
- collecting data for analysis & network research - Security analysis
- Detecting unauthorized access and security vulnerabilities
Just as with reconnaissance, there are multiple types of network sniffing. Passive and active.
Passive network sniffing is when the monitoring and capture of traveling data packets is performed without interfering with the network’s operations or alerting targets being monitored. To enable this, you would place the network interface card (NIC) in promiscuous mode. This allows the NIC to capture all traffic on a particular network segment, no matter the destination address.
A more intrusive approach concerns active network sniffing. Here, new traffic and carefully crafted packets are introduced into a network to gain access to data. Adversaries will use this method to gain unauthorized access to login credentials or confidential communications though it requires much more careful planning and execution. This version of sniffing is often used in switched networks where traffic is not broadcasted extensively.
We will now take a closer look at the numerous techniques that can be used in conjunction with active network sniffing.
- ARP Spoofing (also known as ARP poisoning)
ARP (Address Resolution Protocol ) is a critical communication protocol that operates at the link layer of the OSI model. It is used for discovering the MAC address and thus, devices in a network and was defined in 1982 by https://datatracker.ietf.org/doc/html/rfc826. Due to a lack of reply authentication, attackers can send false ARP messages over a network with the goal being to associate their MAC address with the IP of another device. This will eventually lead to traffic being sent to the attacker, allowing them to intercept, modify or disrupt communication between devices on the network.
ARP spoofing can lead to man-in-the-middle attacks, DoS and session hijacking. Good prevention methods for the attack include configuring static ARP entries for critical devices, utilizing dynamic ARP inspection (DAI) on network switches, implementing network segmentation to limit the scope of attacks and using encrypted communication protocols. - MAC Flooding
This network attack technique can be used to compromise the security of network switches by overwhelming the switch’s MAC address table, causing it to fail and revert to ‘fail-open’ mode. In this mode, the switch will broadcast all incoming traffic to all ports like a hub, enabling an attacker to sniff and capture network traffic that would otherwise be inaccessible.
To achieve this attack, adversaries will send a large number of frames with different MAC addresses to a switch at a high rate which will then rapidly fill the table. If successful, a MAC flooding attack can enable the interception of sensitive data, degrade network performance or lead to further attacks.
To help prevent MAC flooding it is recommended to enable port security features on switches to limit the number of MAC addresses that can be learned on a single port. Alongside, MAC address table ageing, VLAN segmentation and network access control are all good defensive measures. - DNS Spoofing
Sometimes called DNS cache poisoning, this attack involves an attacker corrupting a DNS cache with false information, resulting in a DNS resolver returning an incorrect IP address. This is possible through the sending of forged DNS responses to a DNS resolver. If these are accepted, then incorrect information will be stored in the resolver’s cache, affecting future queries. This can result in the redirection of traffic intended for a legitimate website to a malicious, attacker-controlled version. Alternatively, a MitM attack or compromised DNS server are two additional ways in which an attacker can carry this out.
The consequences of DNS spoofing can include phishing and credential theft, malware distribution and data interception. To prevent the attack DNSSEC (Domain Name System Security Extensions ) can be implemented helping to ensure the authenticity and integrity of DNS responses. Alongside, using secure HTTPS connections, regularly updating DNS server software and implementing cache poisoning protection is recommended. - DHCP Spoofing
With DHCP spoofing, a hacker introduces a rogue DHCP server on a network which responds to client requests, providing them with incorrect IPs, gateway addresses and other network configuration parameters. When a client device sends out a DHCP discovery request to obtain an IP address, both the legitimate DHCP server and the rogue server respond. If the latter server’s response is faster then the client will configure itself using the parameters provided by the rogue server.
The consequence of this attack is that traffic will be routed through the attacker’s device or to malicious servers. To help prevent it, it is advised to enable DHCP snooping on network switches. Additional measures include implementing port security, static IP addressing for critical devices, network segmentation and enforcing security policies concerning where DHCP servers can be deployed. - ICMP Redirection
ICMP redirection is a network mechanism that is intended for the optimization of packet routing within a network. Legitimate uses of ICMP redirection include network optimization and dynamic route adjustment. Nonetheless, it too can be exploited by attackers to reroute traffic for malicious purposes.
For example, attackers can send forged ICMP redirect messages to a host, causing it to reroute traffic through the attacker’s device. Alternatively, redirecting traffic through a malicious router or gateway will also enable the capturing of sensitive information. Finally, redirecting traffic to non-existent or incorrect gateways can lead to network disruptions.
Effective prevention methods for ICMP redirection include: disabling the acceptance of ICMP redirect messages on hosts and routers through configuration settings, using secure routing protocols and static routing, configuring firewalls to filter out ICMP redirect messages from untrusted sources and segmenting the network to limit potential impact.
Now that we understand more about the various attacks that can be carried out through network sniffing, let's take a closer look at some of the tools available that can help us analyze these attacks.
Today, three of the most well-known network sniffing and analysis tools used for capturing and analyzing network traffic include:

- operates entirely from the command line
- supports complex filter expressions
- can save captured packets to a file for later analysis with additional tools
- is cross-platform

- has a user-friendly GUI interface
- includes deep packet inspection
- provides real-time capture and analysis
- filtering and coloring
- extensive support for a wide range of network protocols

- has extensible plugin support for additional functionality
- has a GUI and command-line interface
- focuses on MITM attacks
The oldest of the three (tcpdump) was originally released in 1988 and is distributed under the BSD license. To install tcpdump on Linux Ubuntu, you would use the below command:
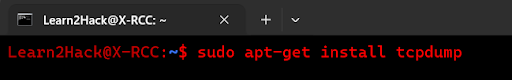
$sudo apt-get install tcpdump
(on RPM-based distributions use: ‘sudo yum install tcpdump’)
For a more in-depth guide on tcpdump, visit the below links:
Defensive Measures
On a general level, to protect against network sniffing, there are multiple mitigation strategies and defensive measures that can be implemented. These include:
- Implement strong encryption protocols for data in transit:
- SSL/TLS for web traffic
- IPSec for IP communications
- WPA3 for Wi-Fi networks
- VPNs to encrypt network traffic
- Have a secure network design:
- Use VLANs and network segmentation to limit the exposure of sensitive data
- Use switches instead of hubs to make it harder for sniffers to capture packets not destined for their ports
- Implement access control:
- Use MAC address filtering to allow only specific devices to connect to the network
- Use Network Access Control (NAC) to enforce security policies, authenticate devices and control network access
- Network Monitoring and Detection:
- Deploy IDS/IPS to monitor network traffic for unusual activities that may indicate sniffing attempts
- Use tools that analyze traffic patterns to detect deviations that might suggest sniffing activities
- Physical Security:
- Ensure physical security of network hardware such as routers, switches, and servers to prevent tampering
- Protect and manage network cabling to prevent unauthorized tapping
- Regular Updates and Patching:
- Regularly update and patch network devices and software to protect against vulnerabilities that could be exploited for sniffing
- Ensure that firmware for network equipment is current and security patches are applied promptly
Case Studies
The 2015 Ukraine power grid attack was a sophisticated cyberattack that resulted in significant power outages across several regions in Ukraine. Network sniffing played a critical role in the execution and success of this attack. Let's take a closer look.
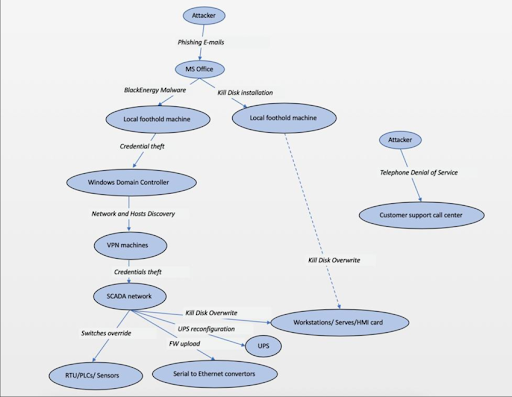
Attack vectors for the Ukraine Power Grid Attack in 2015
Background of the Attack:
- Date: December 23, 2015
- Target: Ukrainian power distribution companies
- Impact: Approximately 230,000 people were left without electricity for several hours.
Steps Involved in the Attack:
- Initial Compromise:
- The attackers gained initial access to the networks of Ukrainian power companies through spear-phishing emails. These emails contained malicious Microsoft Office attachments that, when opened, installed BlackEnergy malware on the targeted systems.
- Establishing Persistence:
- The malware allowed the attackers to establish a foothold in the network and maintain persistent access. They used this access to deploy additional tools, including the KillDisk malware, which was designed to wipe data and render systems inoperable.
- Credential Harvesting:
- Once inside the network, the attackers used various tools and techniques to escalate their privileges. This included network sniffing to capture credentials and authentication data transmitted within the internal network.
Role of Network Sniffing:
- Monitoring Network Traffic:
- The attackers employed network sniffing tools to monitor internal network traffic. By doing this, they could capture unencrypted communication between systems, including usernames and passwords used by employees to access critical systems.
- Capturing Credentials:
- Network sniffing allowed the attackers to capture the credentials of users with higher privileges, such as administrators who had access to the Industrial Control Systems (ICS) and SCADA (Supervisory Control and Data Acquisition) systems that managed the power grid.
- Gaining Access to Critical Systems:
- Using the captured credentials, the attackers were able to remotely access and control the ICS/SCADA systems. They then used this access to open circuit breakers at substations, leading to power outages.
This incident underscored the importance of securing network communications, implementing strong authentication mechanisms, and monitoring unauthorized activities to protect critical infrastructure from similar threats.
For more reading visit:
